RISK MANAGEMENT
Risk Management Policy and Procedures
To promote sustainable operations, strengthen corporate governance, and enhance the risk management framework, the Board of Directors of Catcher Technology approved the adoption of the “Risk Management Policy and Procedures” on November 6, 2024, with the Audit Committee overseeing risk management matters. To further strengthen risk management and sustainability governance, the Company established the Sustainability Development and Risk Management Committee under the Board of Directors on November 6, 2025. The Committee is responsible for overseeing risk management–related matters, while the Sustainability Development Office coordinates and consolidates risk issues and implements risk management activities. The Sustainability Development Office reports at least annually to the Sustainability Development and Risk Management Committee and the Board on the operation and outcomes of the Company’s risk management framework.
The Company’s risk management framework covers environmental risks (including climate change, biodiversity, occupational health and safety, and energy management), social and human rights risks, corporate governance risks (including legal and regulatory compliance, anti-corruption and fraud prevention, and information security), financial risks, and other operational risks. The risk management process encompasses key stages such as risk identification and analysis, risk assessment, risk response, and monitoring and review mechanisms. Relevant departments regularly identify risk items based on their operational responsibilities and, in accordance with materiality principles and stakeholder concerns, conduct risk identification and analysis to assess the potential impact of each risk on the Company’s operations. Based on these assessments, appropriate risk management measures and mitigation strategies are formulated to enhance operational resilience.
For details, please refer to our company's Policies and Procedures for Risk Management.
Risk Management Organization and Responsibilities
Risk Management Levels and Responsibilities:
- First line of defense: Each business or management unit is responsible for implementing risk identification, assessment, monitoring, and response measures in accordance with the Risk Management Policies and Procedures as part of daily operations and management activities.
- Second line of defense: The Internal Audit Department conducts regular audits and reviews to evaluate the adequacy and effectiveness of each unit’s risk management systems and implementation. Improvement recommendations are provided to ensure the continuous effectiveness of risk control.
- Third line of defense: The Sustainability Development Office, under the supervision of the Chairman, is responsible for coordinating overall risk management, consolidating implementation results from various units, and regularly reporting to the Sustainability Development and Risk Management Committee and the Board of Directors to ensure the ongoing enhancement of the Company’s risk management framework.
Overview of Risk Management Operations
Catcher actively implements its risk management system and continuously strengthens the identification, assessment, and control of various risks. On November 6, 2025, the Sustainability Development Office presented the annual report on the Company’s risk management operations to the Audit Committee and the Board of Directors. The key highlights are summarized as follows:
1. Identification, Analysis and Assessment of Key Risk Issues
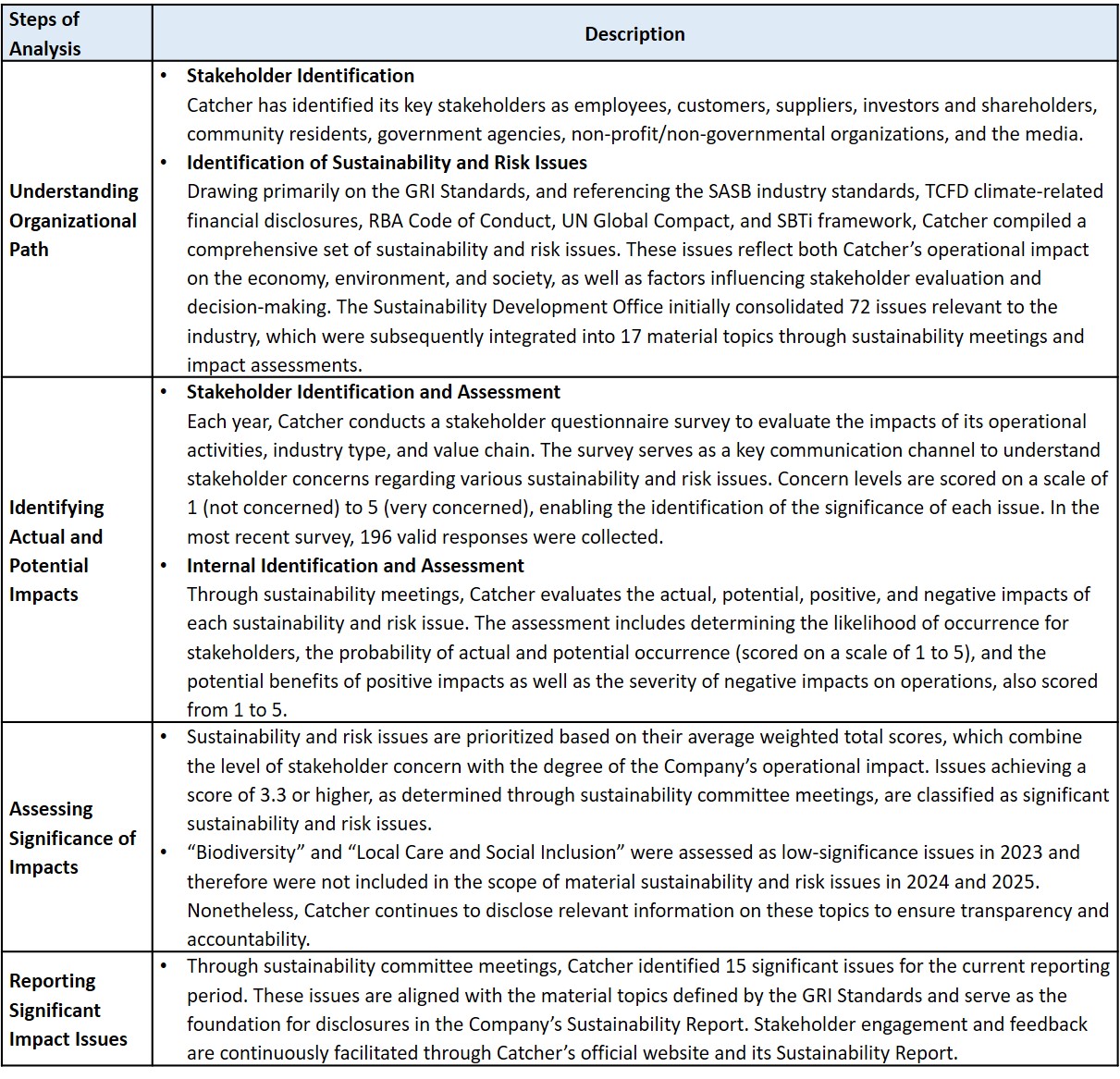
2. Results of the Identification of Significant Impact Issues
(A total of 15 significant issues were identified during the current reporting period)
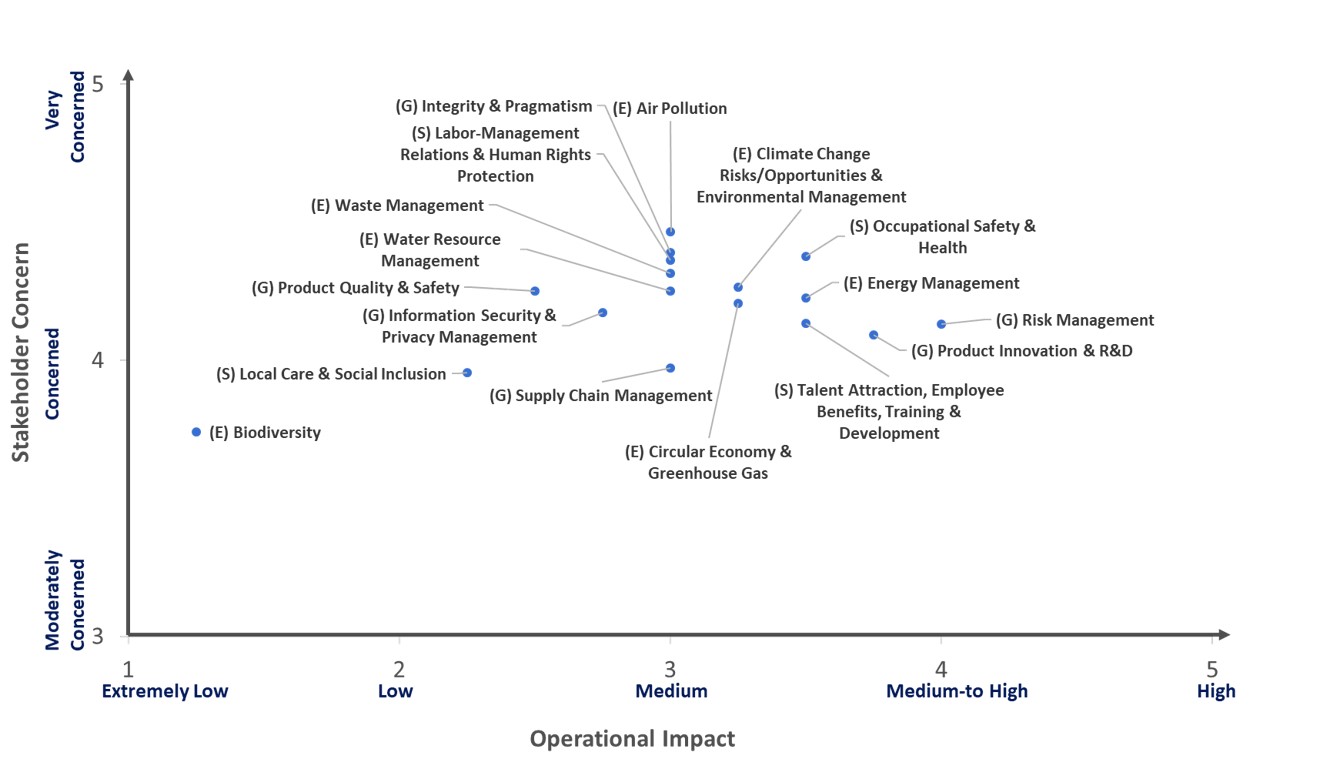
Weighted Quantitative Scoring of Significant Impact Issues for the Current Period
*Biodiversity and Local Care and Social Inclusion were assessed as low-significance issues in 2023 and, therefore, were not included within the scope of material sustainability and risk issues in 2024 and 2025. Nonetheless, Catcher continues to disclose relevant information on these topics to ensure transparency and demonstrate its ongoing commitment to environmental protection and community engagement.

3. Risk Management Operations
For each major risk issue, Catcher has established corresponding risk management mechanisms, procedures, and regulations. To date, no significant irregularities or major incidents have occurred, and all risk mitigation measures have been effectively implemented and monitored, demonstrating Catcher’s commitment to proactive risk control and operational resilience.
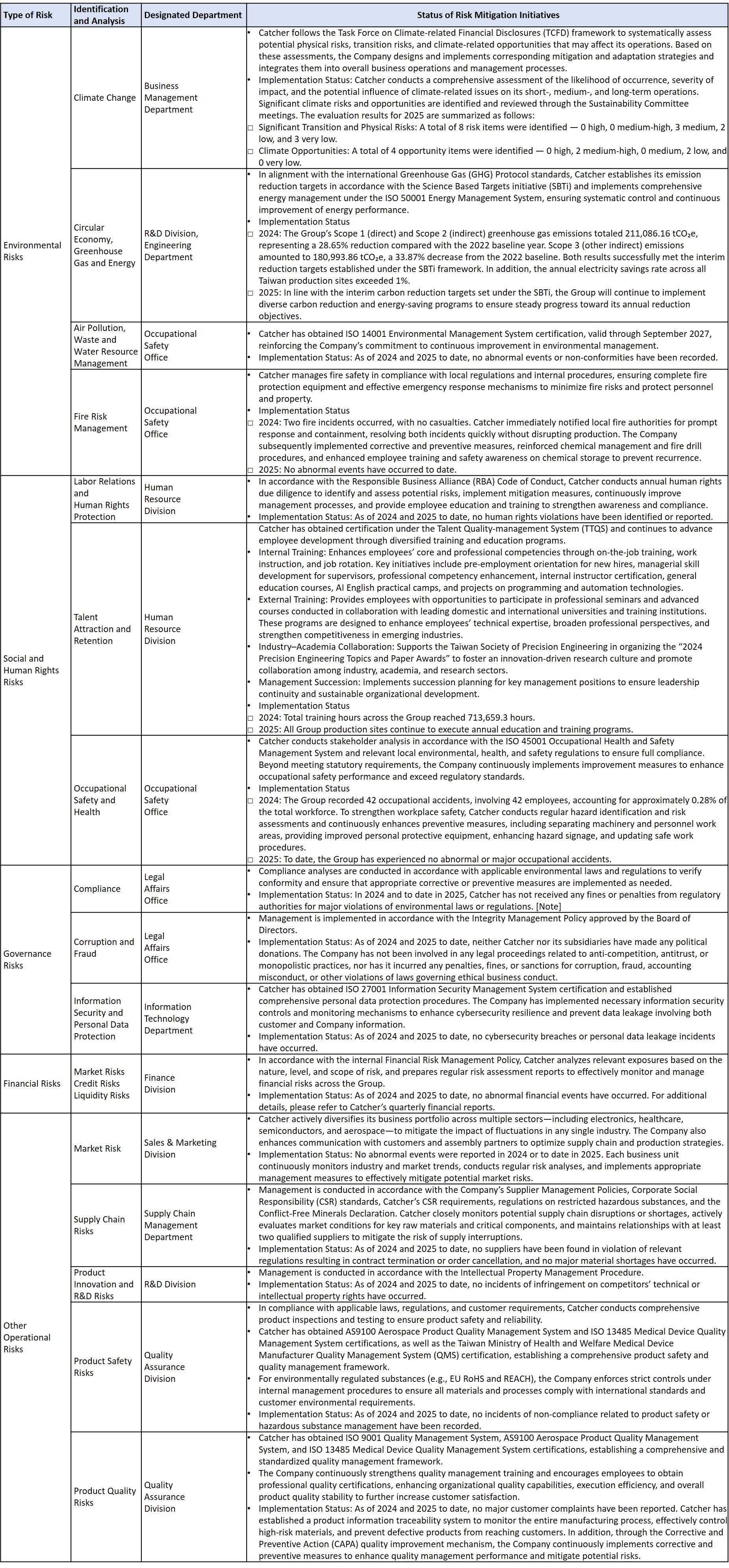
Note: Under the Taiwan Stock Exchange Corporation’s Procedures for Verification and Public Disclosure of Material Information by Listed Companies, any single event with cumulative fines of NT$1,000,000 or more is classified as a material event.
Information Security Risk Management Framework
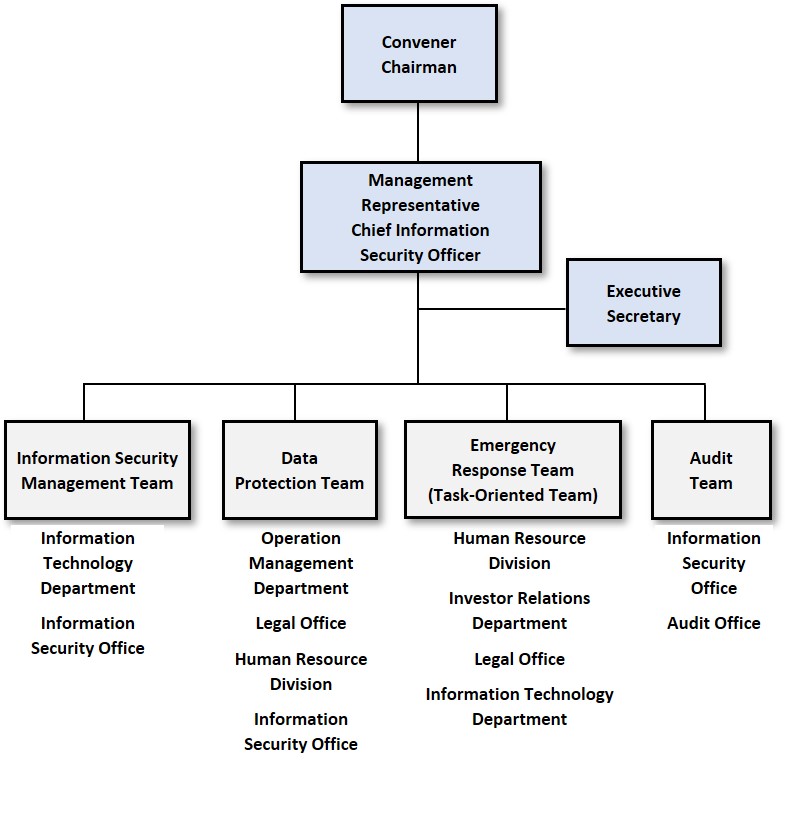
Catcher Technology has established an Information Security Promotion Task Force, comprising a Convener, Management Representative, Executive Secretary, Information Security Management Team, Data Protection Team, Emergency Response Team (task-oriented), and Audit Team. The Task Force is responsible for formulating the directions and strategies for the Company’s information security development, and for promoting and implementing the initiatives related to information security management to ensure the continuous and stable operation of the information security management system.
- Information Security Promotion Task Force: The Company’s decision-making and management body for information security, responsible for overseeing and coordinating information security initiatives.
- Management Representative: Responsible for the overall planning of information security–related systems, coordination of resources, and implementation of related projects.
- Executive Secretary: Assists the Management Representative and the Convener in carrying out information security management duties.
- Information Security Management Team: Responsible for the planning, establishment, implementation, maintenance, review, and continual improvement of the Company’s information security management system; reports information security–related matters to the Information Security Promotion Task Force; coordinates and confirms audit schedules; oversees audit execution; and supervises preventive and corrective actions.
- Data Protection Team: Responsible for promoting and implementing management systems for data and personal data protection.
- Emergency Response Team: A task-oriented team responsible for monitoring and tracking the development of major information security incidents, and for maintaining, updating, and executing disaster recovery procedures.
- Audit Team: Responsible for formulating information security–related audit plans, conducting audits, and tracking preventive and corrective actions for any nonconformities identified during audits.
Information Security Policy
Catcher Technology is committed to information security management. Through comprehensive management systems and technical controls, the Company safeguards its products, services and information assets, prevents unauthorized access, alteration, use and disclosure, and mitigates potential losses arising from natural disasters and other unforeseen incidents. The Company ensures the timeliness, integrity and availability of information to protect the confidentiality, integrity and availability of critical information assets, while complying with applicable laws and regulations. These efforts are aimed at strengthening customer trust, fulfilling commitments to shareholders, and ensuring the continuity of critical operations and the Company’s sustainable development.
- Organization-wide participation to enhance information security awareness: Foster a culture in which information security is everyone’s responsibility through full participation and continuous education and training.
- Proactive prevention and effective information security management: Establish robust information security protection technologies, implement an information security management system, and continuously review and enhance management effectiveness through the Plan–Do–Check–Act (PDCA) cycle.
- Customer trust and sustainable operations: Provide a secure, stable, and trusted operating and manufacturing environment to ensure the Company’s long-term, steady business development.
Information Security Management Program
To demonstrate the Company’s commitment to information security management and to ensure that all information assets and systems are appropriately protected, the Company has established, documented, implemented and maintained an Information Security Management System (ISMS) in accordance with ISO/IEC 27001:2022. Through continual improvement mechanisms, the Company continuously enhances the effectiveness of the system’s operation.
Objectives
- Implement appropriate protection and security measures for all information stored, processed, or transmitted by the Company.
- Reduce the likelihood and impact of information security incidents involving damage, theft, leakage, tampering, misuse, or infringement of information assets.
- Continuously strengthen the confidentiality, integrity, and availability of information services and systems across all operational processes.
Information Security Management Measures
In accordance with ISO/IEC 27001:2022, Catcher Technology adopts the Plan–Do–Check–Act (PDCA) cycle to establish and implement its Information Security Management System, ensuring effective operation and continual improvement.
- Establish a comprehensive information security governance structure responsible for promoting information security policies, facilitating cross-departmental coordination, and overseeing implementation.
- Conduct management reviews at least annually to ensure the appropriateness, adequacy, and effectiveness of the ISMS; review items including improvement initiatives, significant requirements, and assessments of the impact of material changes in the operating environment.
- Define and continuously monitor key performance indicators (KPIs) for information security to evaluate performance and the overall effectiveness of the ISMS.
- Perform information security assessments and audits on a regular basis or as needed to verify compliance with legal requirements and information security standards for control objectives, measures, and operating procedures; implement corrective actions and ongoing maintenance in accordance with plans to continuously enhance the maturity and effectiveness of the ISMS.
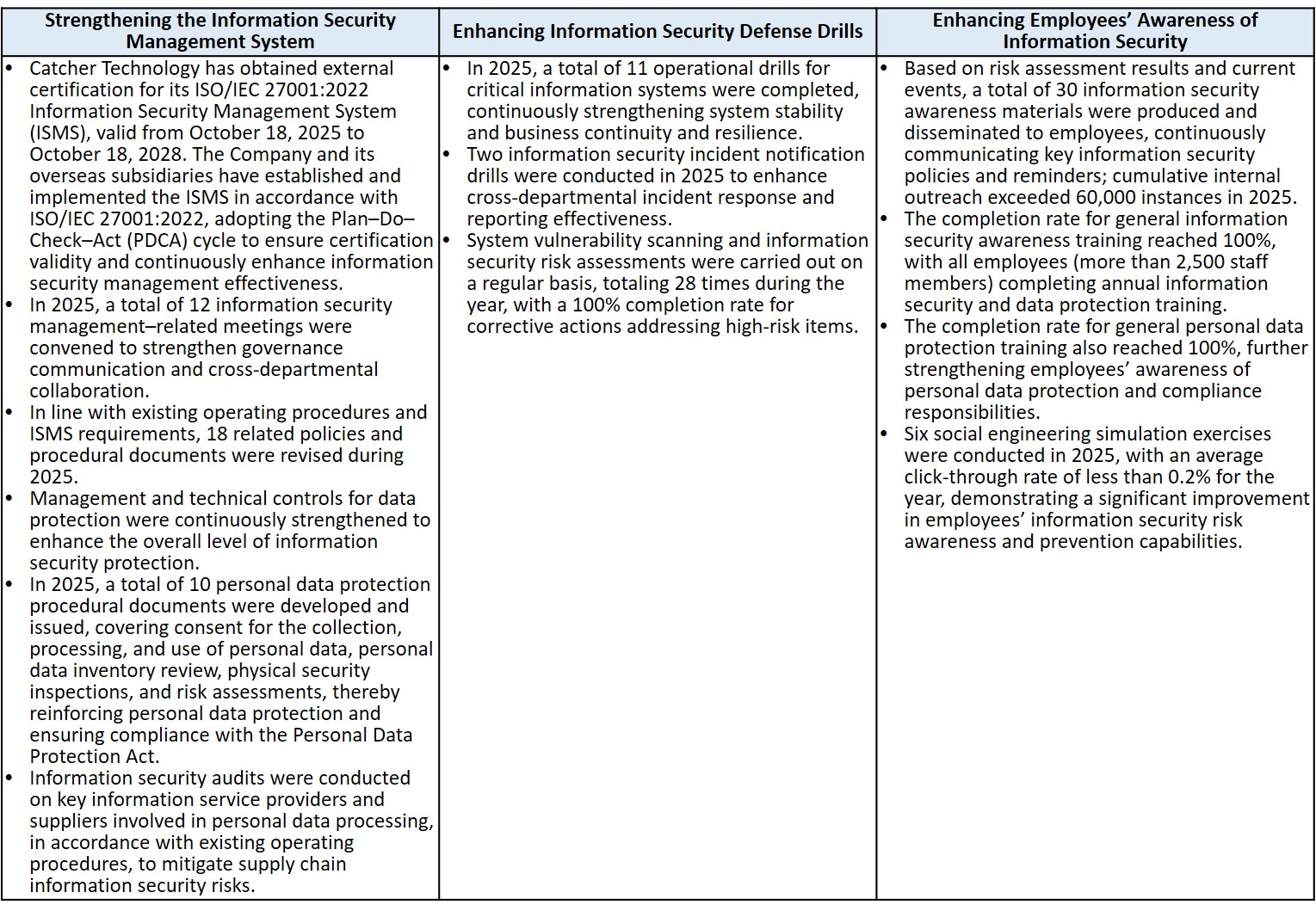
Achievements of Information Security Management
SEARCH
Start typing keywords to discover the service, support, or details you’re looking for.

PRIVACY POLICY
Welcome to the “Catcher Website” (hereinafter referred to as "this website"). To help you use our services and information with peace of mind, we hereby explain our privacy policy to safeguard your rights. Please read the following carefully
01. Scope of the Privacy Policy
This policy covers how this website handles personal information collected when you use its services. It does not apply to websites linked from this site, nor to personnel not managed or authorized by this website.
02. Collection, Processing, and Use of Personal Data
When you visit this website or use its services, we may ask you to provide necessary personal data depending on the nature of the service, and your data will be processed and used solely for that specific purpose. Without your written consent, your data will not be used for any other purposes. When using interactive features such as contact forms or surveys, this site may retain your name, email address, contact information, and usage time. During general browsing, the server will automatically record your IP address, usage time, browser type, and browsing data. This information is used internally to improve our services and will not be shared externally.To provide accurate services, we may conduct statistical analysis on collected survey data. The results may be published as statistical summaries or explanatory text for internal research or public reference, but they will not contain personally identifiable information.
03. Data Protection
The servers of this website are protected with firewalls, antivirus software, and other security measures to safeguard your personal data. Only authorized personnel have access to your data, and all relevant staff have signed confidentiality agreements. Any violations will be subject to legal penalties.When outsourcing services that involve personal data, we will strictly require contractors to uphold confidentiality obligations and implement necessary audits to ensure compliance.
04. External Links
This website may contain links to other websites. However, our privacy policy does not apply to those sites. You must refer to the privacy policy of each linked site.
05. Sharing Personal Data with Third Parties
This website will never provide, exchange, rent, or sell your personal data to any individuals, organizations, private companies, or public agencies unless required by law or contractual obligations.Exceptions include but are not limited to:
01. With your written consent
02. As required by law
03. To prevent danger to your life, body, freedom, or property
04. When cooperating with government agencies or academic institutions for statistical or research purposes in the public interest, and the data is processed in a way that makes individuals unidentifiable
05. When your behavior on the website violates our terms of service or causes harm to other users or third parties, and disclosure is necessary for identification, legal action, or contact
06. When it benefits your rights and interests
07. When we outsource vendors to collect, process, or use your data, and we will oversee them to ensure proper handling
06. Use of Cookies
To provide you with the best service, this website will place and access cookies on your device. You may set your browser’s privacy settings to high to refuse cookies, but doing so may cause some website features to function improperly.
07. Amendments to the Privacy Policy
This website’s privacy policy may be revised at any time to meet changing needs. All updates will be posted on this site.



